NEW - Evacuation Wristbands
A single software for healthcare operators
A single platform for healthcare operators to onboard & schedule employees or agency, improve their reimbursement, standardize compliance programs, provide mock survey tools, emergency evacuation tracking and so much more.
New features every week. Improvements everyday.
Trusted by over 600+ providers including








Manage everything from incidents to budgets in one system
We reduce software fatigue and centralize all of your operational needs under one umbrella.
Import
Import Your Data
We make it easy to import and connect with your existing tools using our partner integrations or custom API.
Connect
Synchronize with PointClickCare
Connect with your EHR and other patient data platforms to close the patient data care loop.
Consolidate
Consolidate & Cut
We provide baked-in services and features you'd otherwise need to buy yet another software for.
Centralize
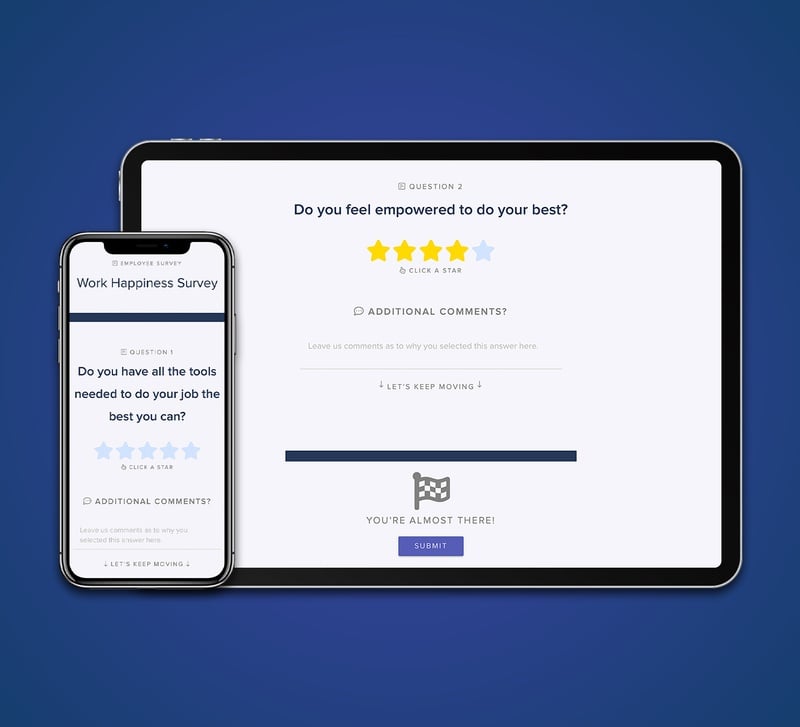
Utilize amazing tools
Harness the power of GreyMAR's toolkits to enhance your community's efficiency, image, and overall security across multiple fronts.

"GreyMAR has simplified so many of our processes. Proactive communication has never been easier and more successful."
Bye-bye dry erase boards
Aaron replaced all of his dry erase/magnetic bed board with GreyMAR's award winning Electronic Bed Board. That's just one tool he's using.
Learn about tools Aaron uses →Some features operators love
Jam packed with 450+ features for as little as $65/month →
Preparedness Booster
Emergencies without the chaos
Enhance your organizations evacuation processes & Disaster Recovery (DR) procedures with GreyMAR's emergency preparedness suite.
-
Track patients completely offline
-
Offline MAR/TAR/KARDEX
-
Compatible with all providers
-
PointClickCare Integrated
-
Offline Policies and Documents
-
Offline Facesheets
-
Evacuation Trackers & Wristbands
-
Offline Allergies
-
Reports & Audit Trails
-
Intuitive and Easy to Use
-
Highly Available Infrastructure
-
On-Demand 24/7 access
-
See more disaster tools →

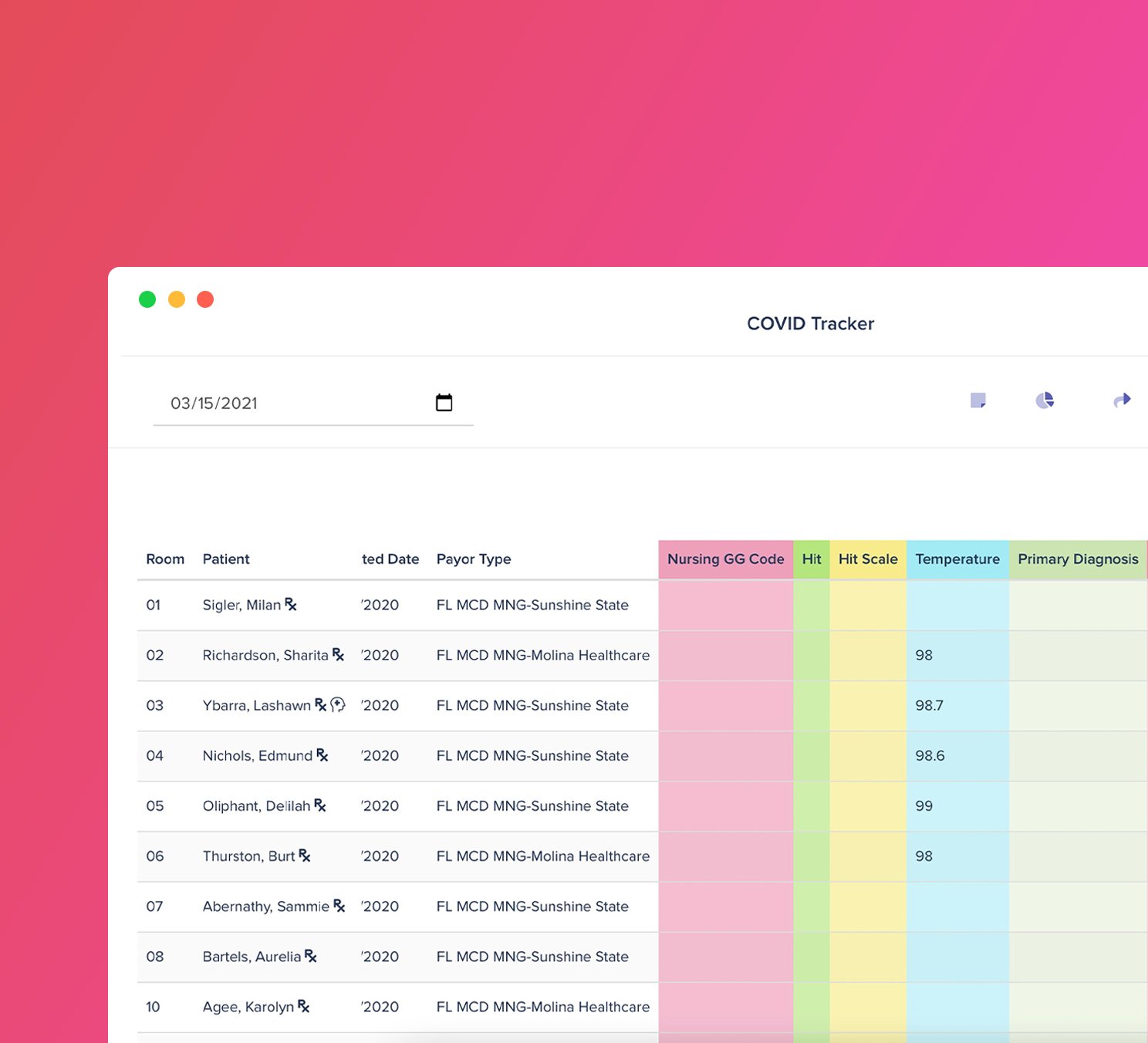
Profitability Booster
Supercharge chart reviews
Find more IPA opportunities with our powerful workspace builders. Build a tracker and add patients to an intelligent care schedule. Scrub documents for NTA opportunities you may have missed.
-
Integrations with popular EHRs
-
Find missing IPA opportunities
-
Enhance UR meetings
-
Scrub Referrals for NTAs
-
Share Documents to Families
-
Dx Scrubbing
-
Build Intelligent Trackers
-
Medication Alerting
-
Change in Care Alerts (CCA)
-
Care Scheduling
-
See more features →
“GreyMAR changed how we connect with families”

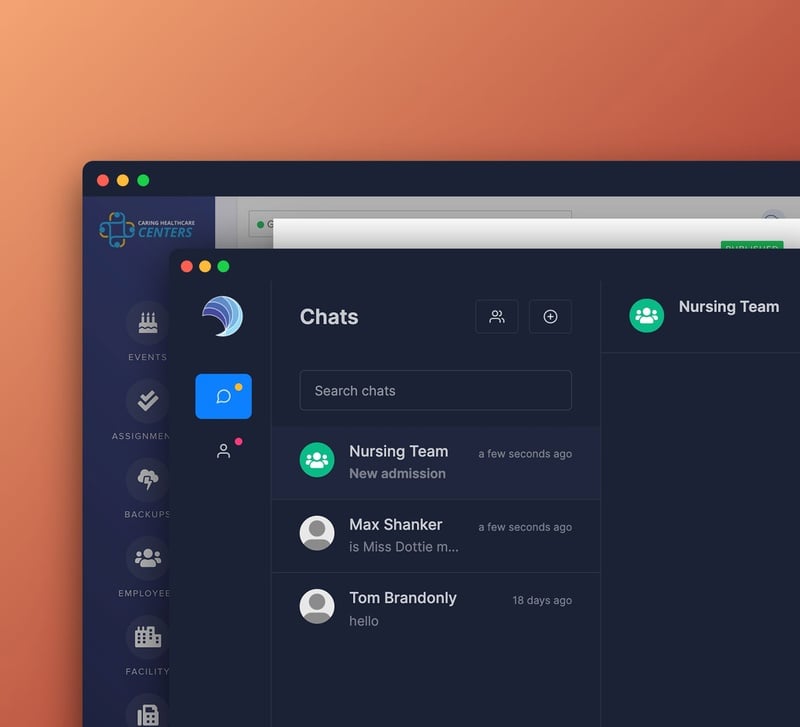
RISK Mitigation
Overhauled clinical workflows
Log your incidents and integrate with WC carriers. Send targeted text messages to families. View patients on a real time bed board. Inventory patient belongings, track rentals, and so much more.
-
Intuitive incident & risk tracking
-
Electronic Admission Agreements
-
Send texts, calls, or emails
-
Progress Note Synchronization
-
Integrated Family Portal
-
Integration with PointClickCare
-
Encrypted-at-Rest data storage
-
2FA Authentication methods
-
Auditing tools and reports
-
Multi-regional high availability
-
See more features →
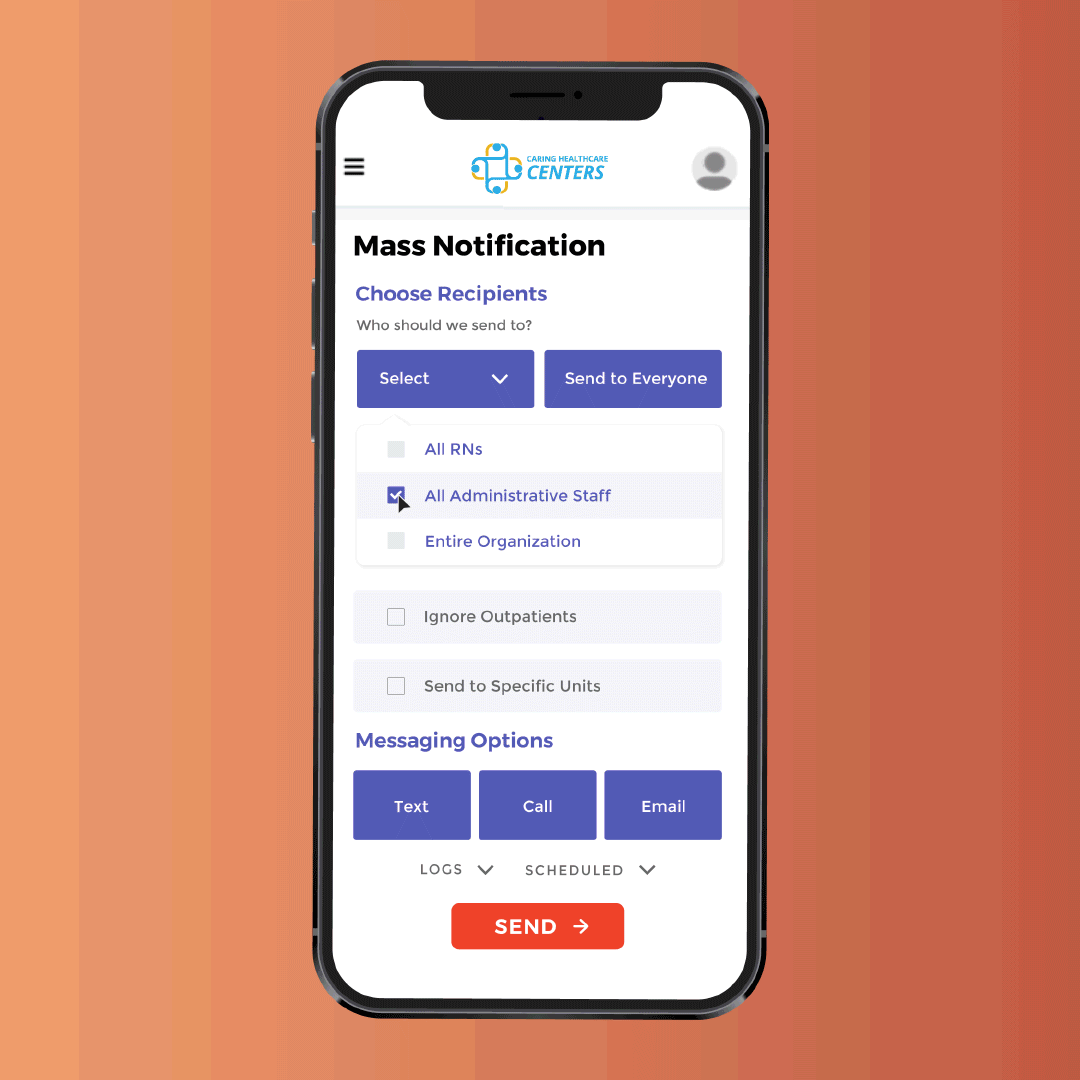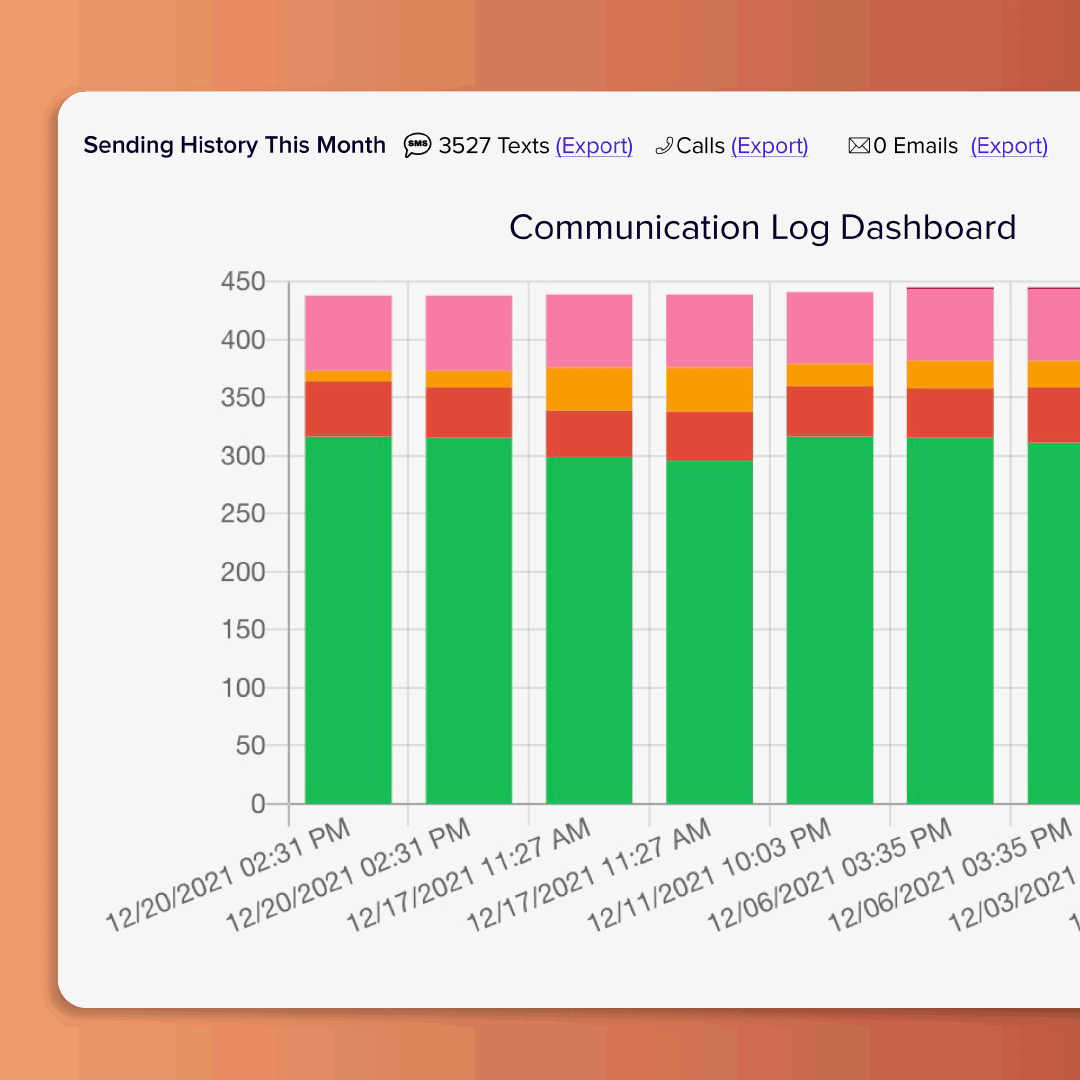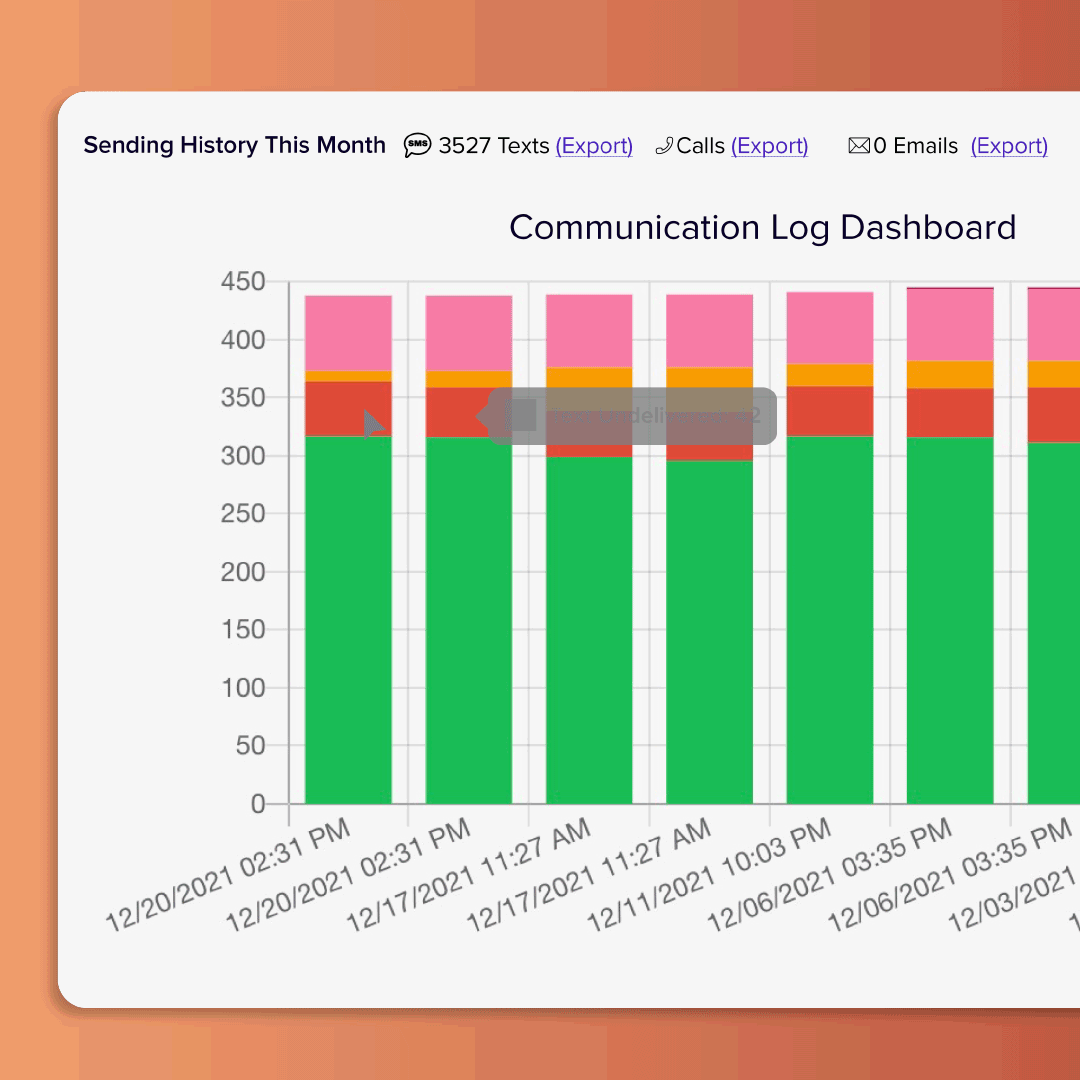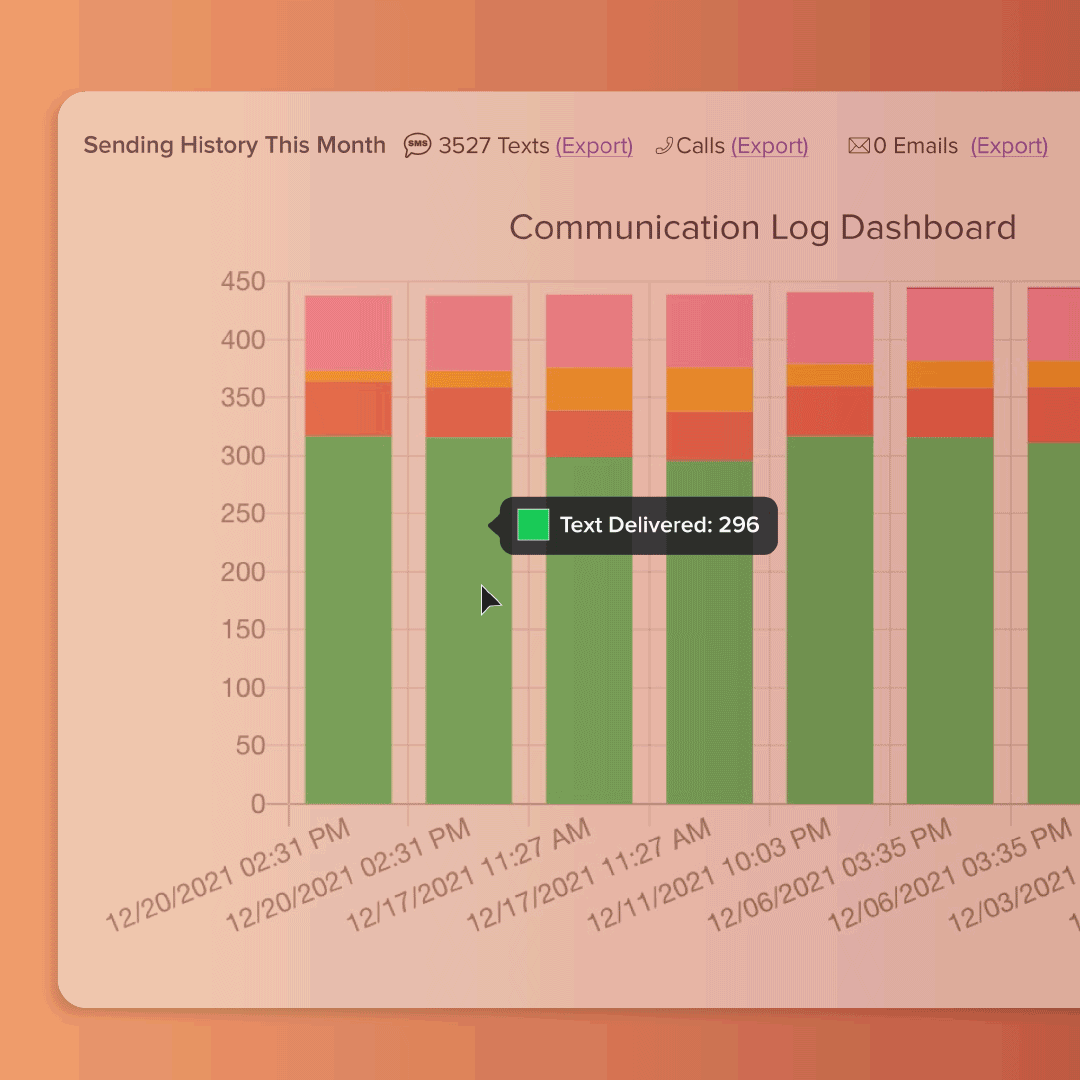
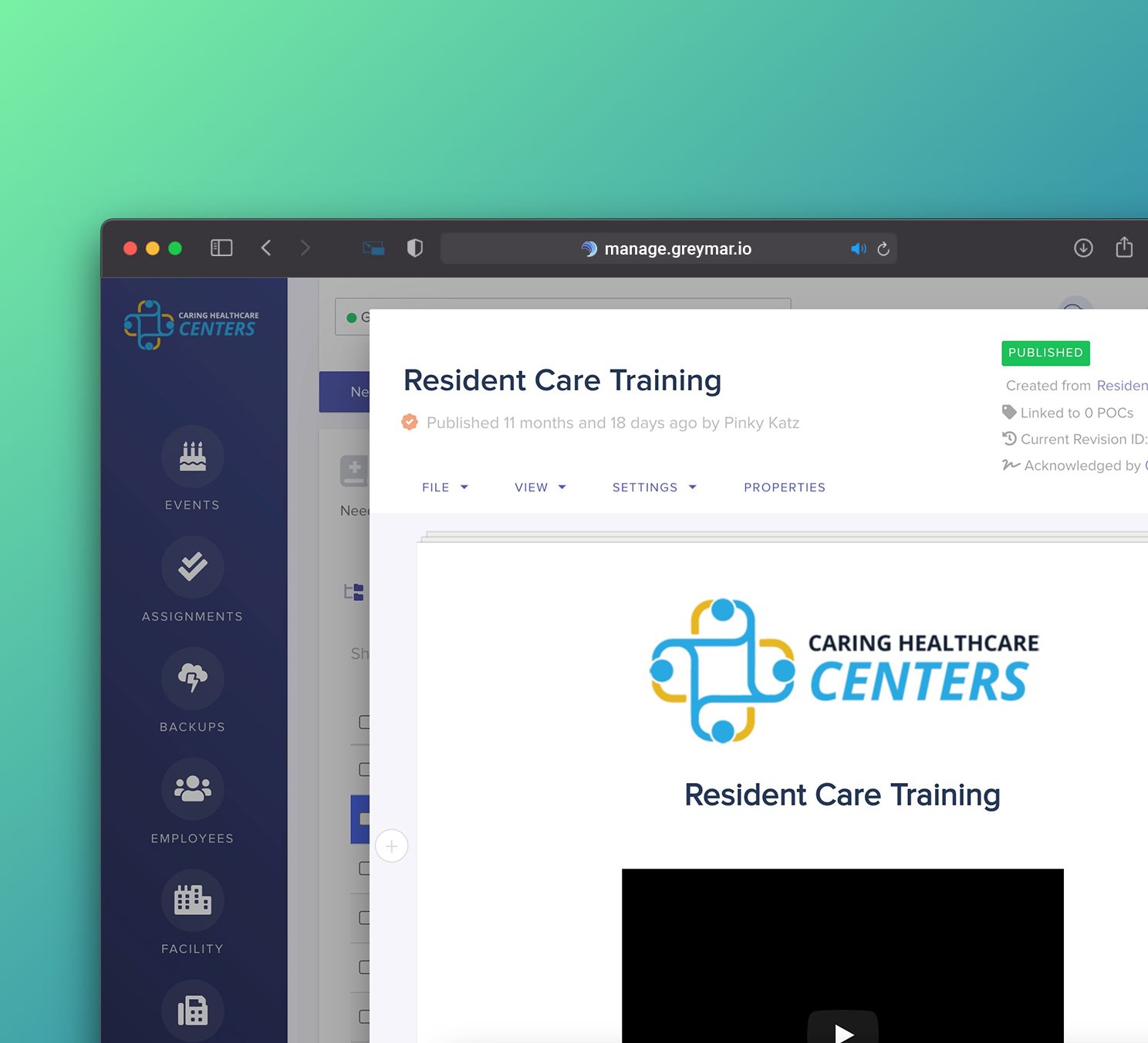
Morale Booster
Integrated onboarding & scheduling
Enhance your staff's experience starting at the onboarding process. GreyMAR features 100% electronic onboarding, scheduling, mass messaging and electronic forms - all in one platform.
-
E-Onboarding for new hires
-
PPD & Immunization Tracking
-
Powerful scheduling
-
Licensure Monitoring
-
Mass messaging to staff
-
Employee Incident Tracking
-
Budget & overtime reports
-
N95 Fitment Test Tracking
-
100% electronic employee file
-
Agency Performance Tracking
-
See more features →
“I have now worked with GreyMAR at two different facilities. The product has grown noticeably and is still very user friendly. They also have the best and most responsive support department in the business!”
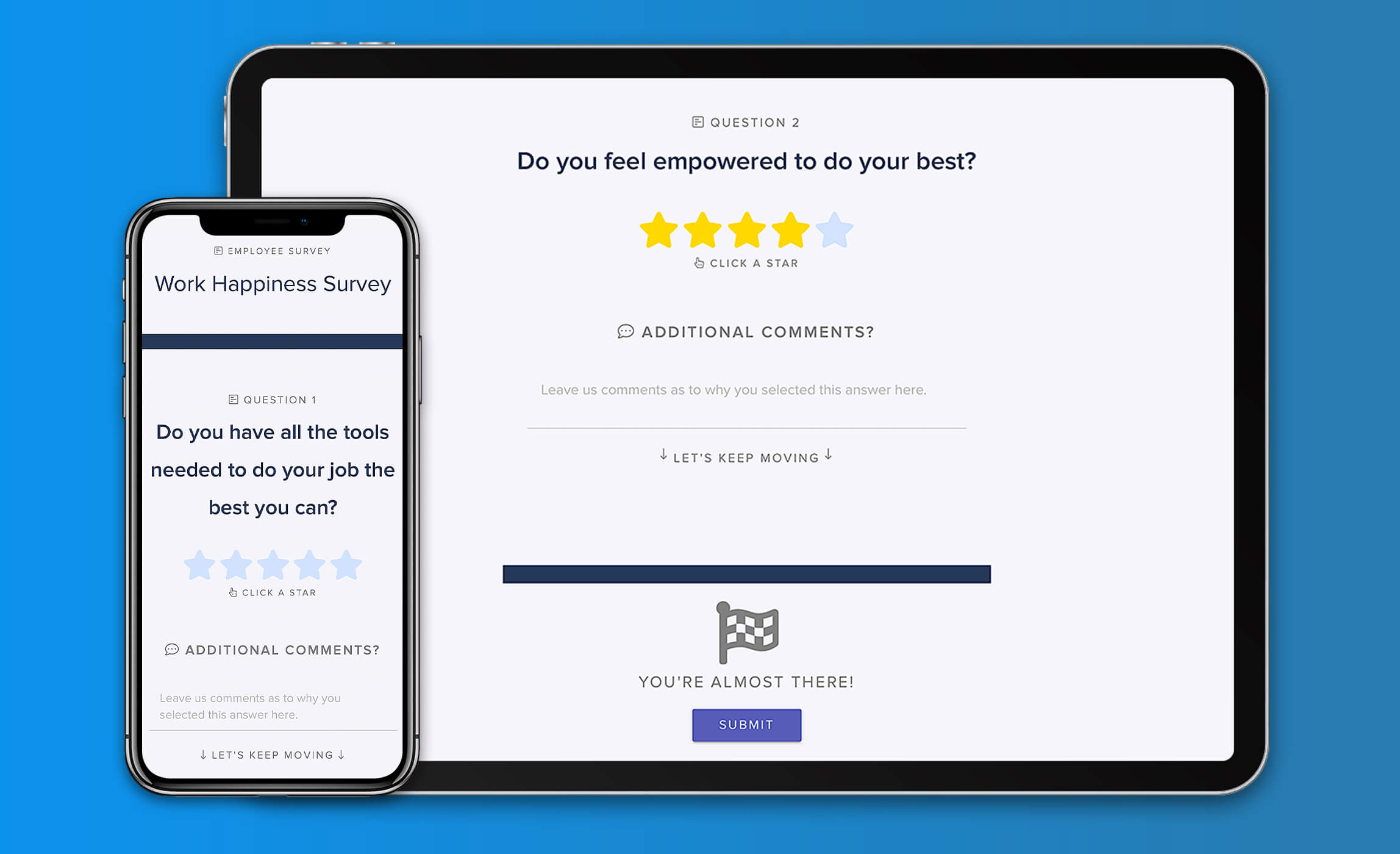
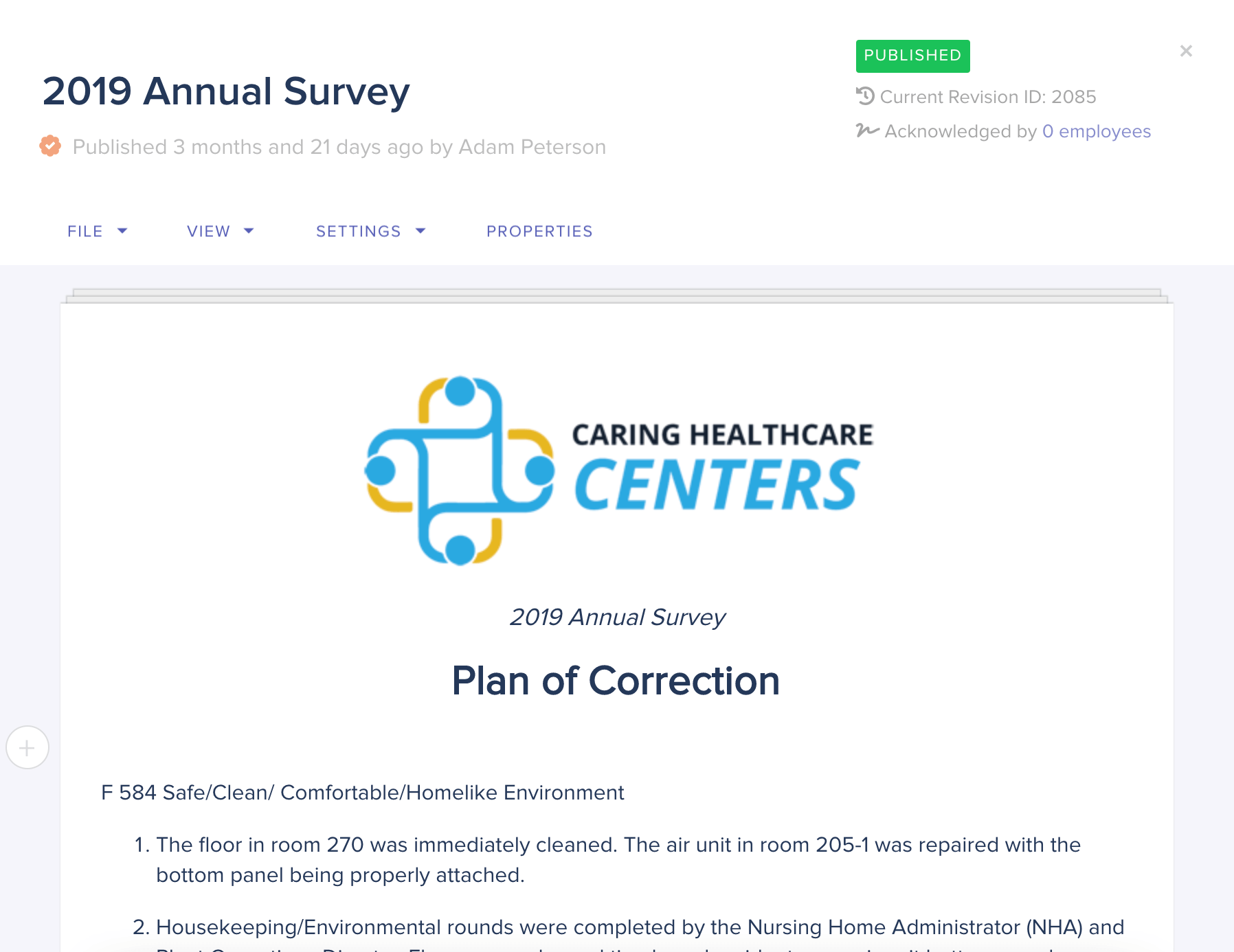
Compliance Booster
Streamline & organize core operations
Organize and streamline overall operations in your facilities. Considered our flagship feature-set, we provide a multitude of state-of-the-art operational tools, survey management and auditing technologies.
-
Policy & Procedure management
-
Survey prep & management
-
Internal auditing & evaluation tools
-
Contract & invoice workflows
-
Maintenance & Life Safety tools
-
Management dashboards
-
Internal education builders
-
CMS & Medicare Integrations
-
Budget dashboards and reporting
-
Customizable look & feel
-
See more features →

...and 450+ more features
We're meticulously designed by operators.
Contact us today to schedule a demo of the entire platform for yourself. Experience GreyMAR today.
Get a demo →